In brief:
- In the U.S., the average cost of a data breach reached a record $10.22 million – a 9% increase over 2024. That’s the highest of any country.
- Cybersecurity doesn’t generate revenue – it protects it – making it challenging to measure ROI and build a business case to justify spending.
- The clearest method for calculating cybersecurity ROI compares investments made with the potential costs of a successful attack – proving the business impact of a proactive security strategy.
- Critical metrics for measuring cybersecurity effectiveness include Mean Time to Detect, Mean Time to Resolve, Reduction in Downtime, and False Positive Rate, among others.
As digital transformation and AI adoption accelerate, so do cybersecurity risks – making it more critical than ever to protect your business from today’s rapidly evolving cyberthreats. Yet for many security teams, measuring cybersecurity ROI remains a challenge – especially when success means preventing problems that never occur.
How do you quantify the value of risk avoided or downtime averted to create an effective business case?
With cybersecurity ranking as the top business risk globally for the fourth consecutive year (Allianz Risk Barometer), it’s clear that security can no longer be treated as a secondary concern.
Many organizations are stepping up to the challenge: the average cybersecurity budget as a percentage of IT spending has increased over the last few years, rising from 8.6% in 2020 to 10.9% in 2025 (IANS Research 2025 Security Budget Benchmark Report). Gartner expects cybersecurity spending to jump 15% in 2025 to $212 billion as AI makes threats faster, smarter, and more lethal than ever before.
Treating cybersecurity as a continuous investment – not a one-time expense – is critical to building long-term financial and operational resilience for your organization as new threats continuously emerge.
Yet, many security teams struggle to secure funding for proactive tools or security initiatives – failing to clearly demonstrate the business impact needed to persuade decision-makers to approve the budget. Unfortunately, that leaves the business reeling when hit by a cyberattack – and suffering the high cost of reactive strategies.
This blog explores why a proactive security posture is not just a business imperative, but a smarter strategy for maximizing security ROI. We’ll help you build your business case by breaking down the key components of proactive investment, the financial toll of security breach recovery, and the core benchmarks for calculating the true value of your cybersecurity spend.
4 urgent reasons cybersecurity investment should be a top priority
The nature, scale, and impact of cyberattacks have ramped up dramatically in recent years for several reasons:
1. AI is making cyberthreats more lethal
AI is supercharging cyberattacks – making them faster, smarter, and harder to stop. Advanced tools like Generative AI and Large Language Models (LLMs) are fueling new, high-impact attack vectors like deepfakes and sophisticated social engineering, while Agentic AI is expected to make it even easier for attackers to hack systems at scale.
- 87% of global organizations experienced AI-powered attacks over the past year (SoSafe’s Cybercrime Trends 2025).
- Only 26% feel confident detecting them.
2. Expanding attack surface creates new vulnerabilities
Digital transformation, cloud adoption, remote work, and sprawling supply chains are multiplying the entry points attackers can exploit to breach your business. Every third-party vendor you work with – and their vendors – adds new vulnerabilities, with the number of third-party breaches doubling since last year (2025 Verizon Data Breach Investigations Report).
Meanwhile, shrinking IT budgets and ongoing labor shortages make it harder to build strong defenses, create a dedicated Security Operations Center (SOC), or invest in advanced tools – leaving many organizations exposed.
3. No business is immune
For far too long, small and medium businesses (SMBs) believed they were relatively safe from the targeted cyberattacks hitting large corporations. Not anymore.
One in three SMBs experienced an attack in the preceding year, with attack costs running as high as $7 million, according to the Microsoft SMB Cybersecurity Report 2024.
Cybercriminals have caught on that the ease of penetrating multiple smaller businesses with weaker defenses can add up to big payoffs. Despite this, the Microsoft study revealed insights into concerning mindsets at small and mid-sized organizations that put them at increased risk:
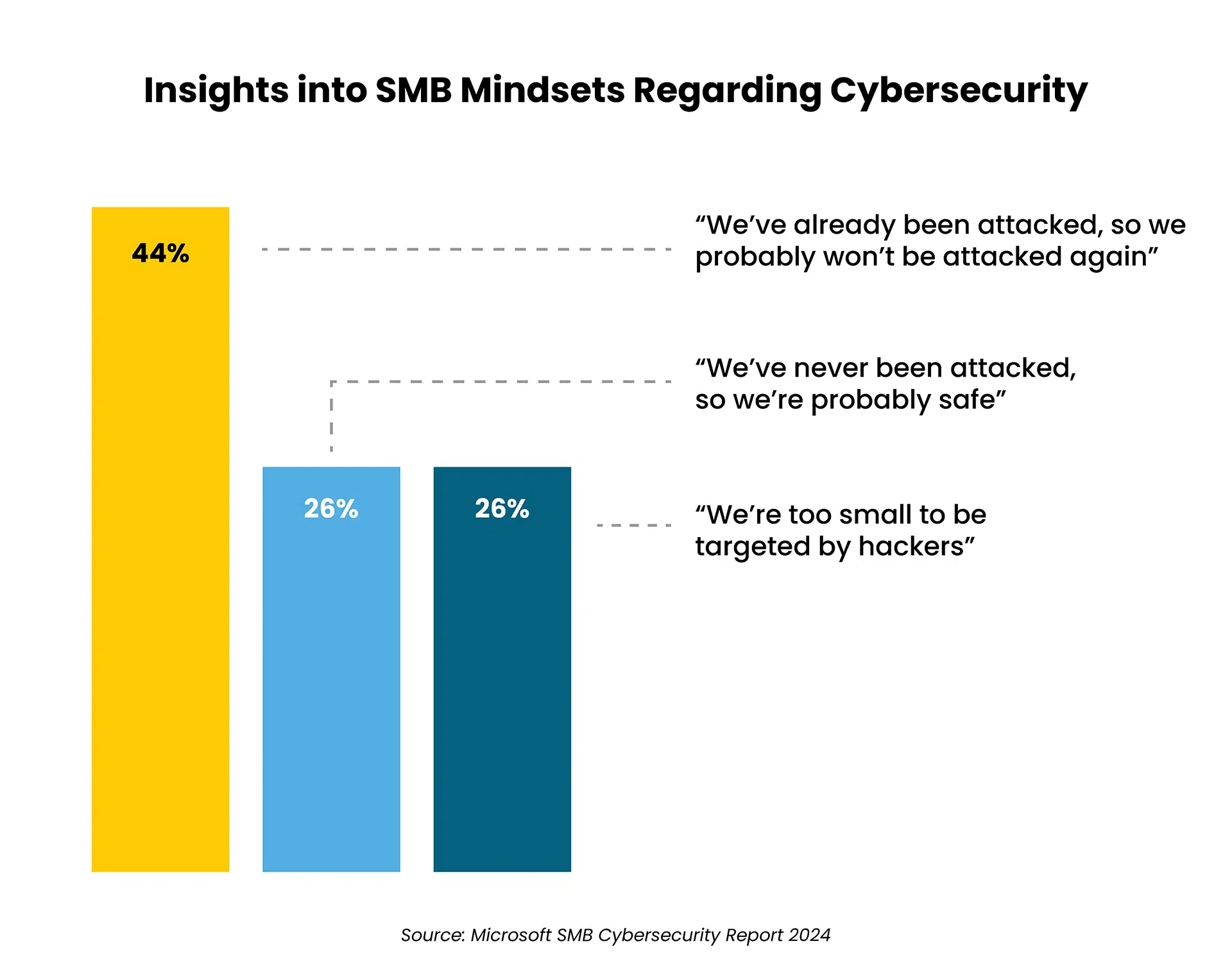
4. Rising cost of cyberattacks in the U.S.
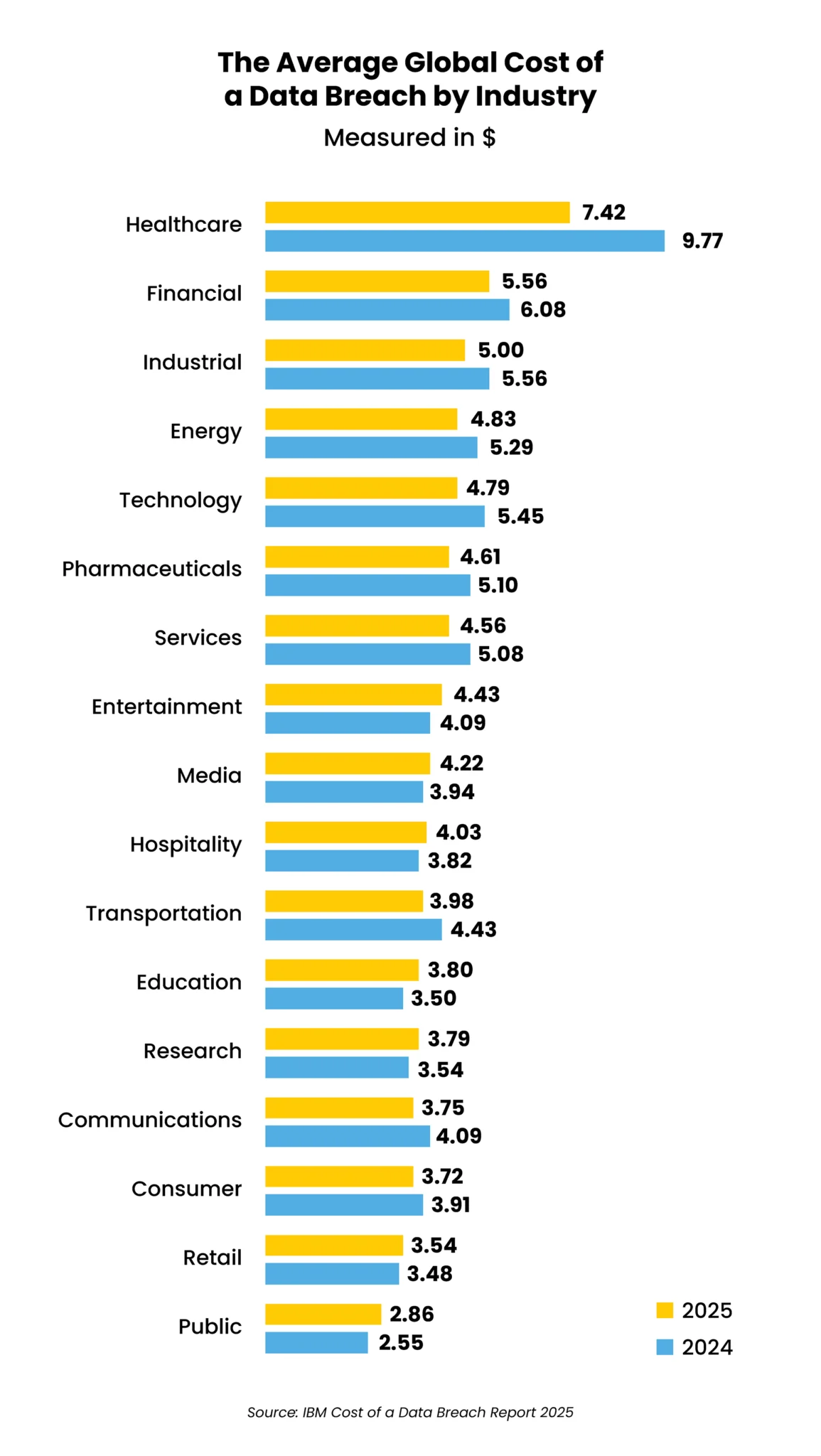
The global average cost of a data breach dropped 9% to $4.44 million in 2025 – the first decline in five years, according to IBM’s Cost of a Data Breach Report 2025. The reason? Improved detection and containment capabilities in organizations, boosted by AI and automation tools, the report states.
But in the U.S., average breach costs surged to a record $10.22 million – a 9% increase over 2024 – driven in large part by higher regulatory fines. That’s the highest of any country.
The takeaway: cybersecurity investments are making an impact – and are vital to avoiding or minimizing the high cost of a successful attack in the U.S.
How to measure cybersecurity ROI: investments versus the cost of an attack
Executive teams prioritize strategic investments with measurable ROI that drive growth and profitability.
But cybersecurity doesn’t generate revenue – it protects it. So, we have to think about its cost-benefit analysis a little differently.
Cybersecurity ROI (return on investment) reflects both the tangible and intangible benefits a business gains from its security investments, relative to the costs. It’s a critical metric for ensuring your cybersecurity spend is strategically aligned toward building a proactive security posture that promotes long-term value, risk reduction, and operational resilience.
This ROI isn’t limited to cost savings from automation or optimized operations – it focuses on avoided losses and improved uptime.
The best method for calculating cybersecurity ROI involves comparing investments made to strengthen your defenses with the potential costs of a successful cyberattack. It’s a clear way to highlight the business case for proactive, forward-looking security strategies.
Another measure that’s often used is return on security investment (ROSI). This calculates the annual loss expectancy – or the anticipated yearly financial cost from a given security risk – before and after a security investment is made, and then divides it by the investment cost. But for this article, we’ll focus on the simpler calculation of IT security ROI.
Let’s dig deeper into what that involves.
Step 1: Add up your cybersecurity investments
Organizations can elevate their threat readiness by investing in three main areas:
1. The right tools
Traditional cybersecurity strategies and siloed solutions are no longer a match for the speed and lethality of AI-powered attacks. To stay resilient, AI-enabled cybersecurity tools capable of detecting, blocking, and responding to this next generation of threats must be part of the security arsenal of every organization.
Some 70% of security professionals say AI has proved highly effective for detecting and stopping threats that would have previously gone unnoticed (2025 Ponemon Institute Report). Case in point: Gartner highlights AI-driven email security as a key trend for reducing phishing exposure in 2025, with independent evaluations showing state-of-the-art AI phishing detection models can achieve up to 97.5% accuracy in identifying malicious emails before they become business-impacting events.
Key investments include threat detection systems to identify patterns and anomalies, AI-driven email security, and automated incident response to stop breaches faster. In addition, critical tools such as firewalls, endpoint detection and response (EDR) solutions, and cloud security tools should be prioritized.
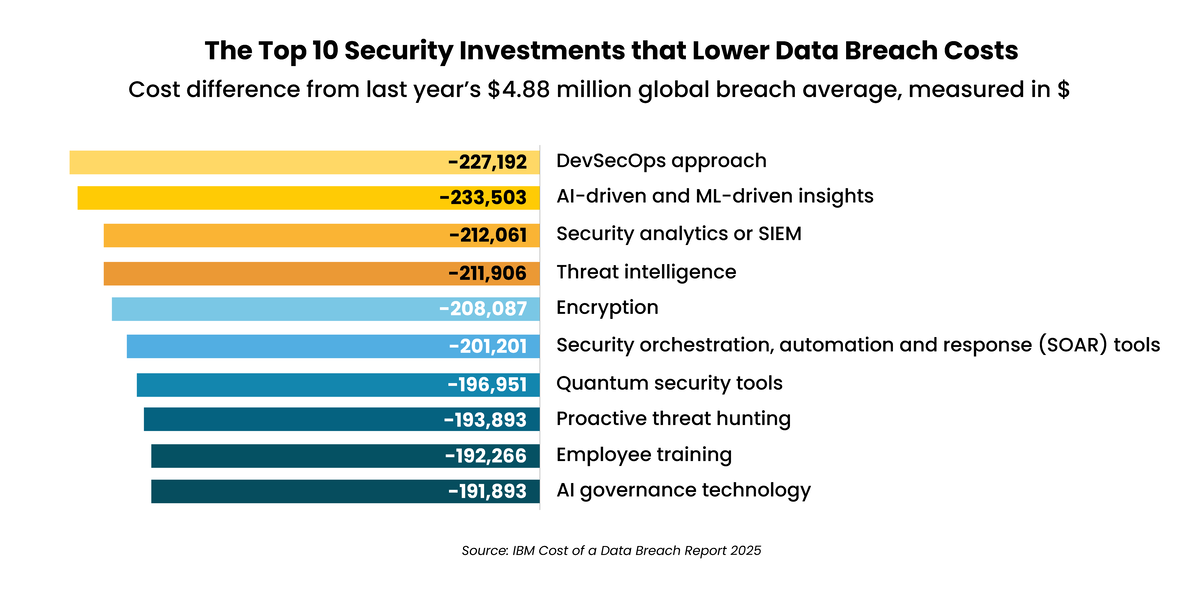
Average savings: Security teams that fully leverage AI and automation in their cybersecurity operations lower breach costs by $1.9 million compared to those that do not, IBM reports. AI-enabled defenses cut breach lifecycles by 80 days, limiting damage and data loss.
2. The right people
Pairing these advanced tools with highly skilled cybersecurity talent is vital to building a strong security stance. While AI tools have significantly enhanced threat detection and response, skilled teams remain essential: interpreting AI-driven insights, spotting nuances that AI might miss, providing oversight, making informed decisions, and responding effectively to more complex situations.
Cybersecurity professionals are also needed to continuously optimize security strategies. More than 60% of organizations that suffered a breach over the past 12 months had an average of 43 cybersecurity tools in place – but they had been misconfigured or poorly integrated to defend against real-world threats.
About half of organizations that suffer a data breach are grappling with a severe cybersecurity skills shortage, IBM found. In fact, the IBM report lists lack of talent as the second-highest driver of breach costs.
Top-tier cybersecurity professionals are in high demand and short supply: In the U.S. alone, there is a shortfall of more than 560,000 cybersecurity specialists, BCG’s 2024 Cybersecurity Workforce Report found. Only 14% of organizations are confident they have the people and skills to adequately protect their organization, states WEF’s Global Cybersecurity Outlook 2025 report.
Not surprisingly, cybersecurity is now the #1 most outsourced business function, with 77% of organizations turning to managed security service providers (MSSPs) to strengthen their security posture (Deloitte Global Outsourcing Survey 2024). MSSPs provide skilled resources as well as comprehensive 24×7 coverage, best practices, and proven security methodologies.
The impact on your bottom line: Organizations with little or no cybersecurity skills shortage experience 30% lower breach costs compared to those with severe talent gaps, IBM found.
3. The right processes and controls
The right processes and controls are critical to ensuring consistent, repeatable, and compliant cybersecurity practices across the organization. They provide a structured approach to harnessing your cybersecurity tools and talent to quickly identify, mitigate, and respond to threats.
Key components include a business continuity plan, risk assessments, access controls, incident response plans, security awareness training, and regular audits and compliance checks. Amid growing AI adoption, organizations also need a framework for securing proprietary data and its usage – and establishing AI governance controls.
Average savings: Having an incident response team and effective response framework alone reduces average breach costs by nearly $500,000, IBM found. Employee training is also vital as phishing emerges as the most common attack vector – costing organizations an average $4.8 million per breach, the report found.
Step 2: Add up the cost of a cyberattack
Cyberattacks hit businesses more than 1,900 times per week in early 2025 (Check Point’s 2025 Cyber Securiy Predictions report). Nearly 90% of IT and security leaders at a recent Auxis webinar said they believe an AI attack will disrupt their operations this year.
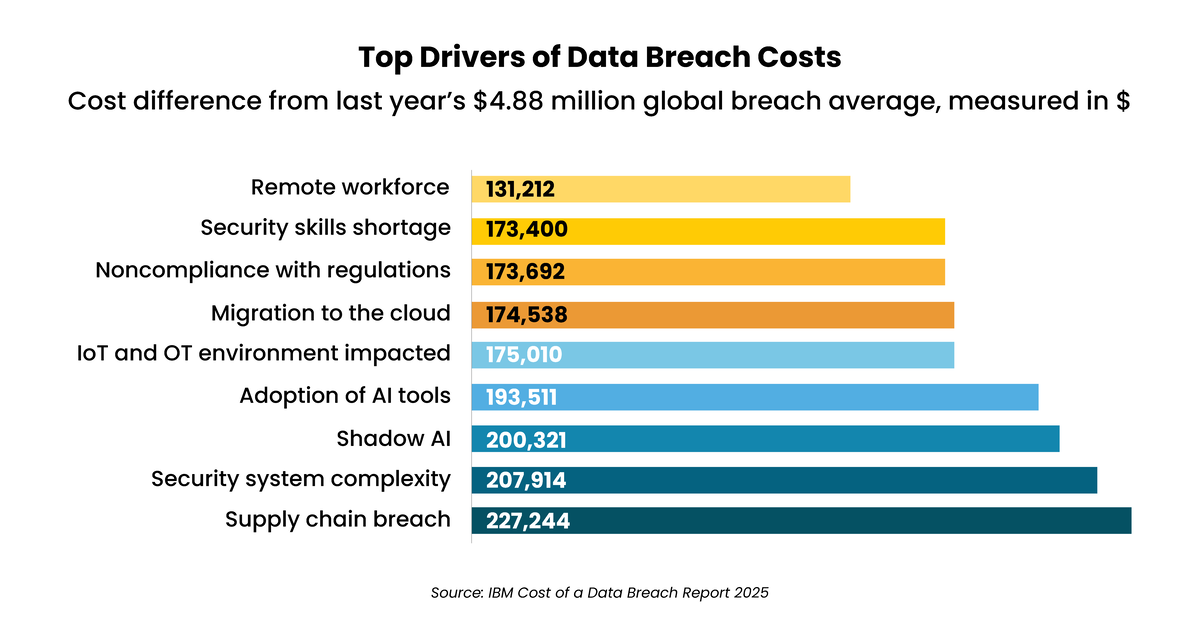
It only takes one successful breach to inflict millions of dollars’ worth of damage. Here are the top drivers behind the average global breach cost of $4.44 million – and staggering $10.22 million cost in the U.S., according to IBM:
1. Lost business/productivity
This includes:
- Lost revenue as system downtime stops customers from accessing services or completing transactions
- Lost employee productivity
- Lost customers
- Having to acquire new customers
- Reputational damage and diminished goodwill
Average global cost: $1.38 million
2. Detection and escalation
This spans:
- Forensic and investigative activities
- Assessment and audit services
- Incident response
- Crisis management
- Communications to executives and boards
Average global cost: $1.47 million – representing a third of total breach costs for an organization.
3. Notification
Activities that enable an organization to notify data subjects, data protection regulators, and other third parties:
- Emails, letters, outbound calls, or general notices to data subjects
- Communication with regulators
- Engagement of outside experts
Average global cost: $390,000
4. Post-breach response
All the activities and resources a business must deploy after a cybersecurity incident has occurred to recover operations and meet legal, regulatory, and customer obligations, including:
- Public relations and brand management
- Victim support (help desk, credit monitoring, etc.)
- Regulatory fines and settlement
- Business and data recovery
Average global cost: $1.2 million – skewing higher in the U.S., where a patchwork of federal and state fines can impose sanctions for the same incident. Nearly half (48%) of regulatory fines now exceed $100,000.
5. Long-term costs
Impacting an organization for months or even years after an attack, affecting revenue, brand reputation, and operational efficiency. This includes:
- Litigation settlements
- Insurance impacts
- Upgraded security infrastructure and monitoring tools
- Compliance upgrades
- Expanding security teams
- Additional employee training
- Policy and procedure overhauls
- Ongoing reputational damage and lost customers
- Diminished customer acquisition rates
Average cost: IBM has shown that long-term expenses can reach 60% of data breach costs, translating to an average of $1.76 million globally and $6.13 million in the U.S. In highly regulated industries like healthcare and financial services, long-term costs average $2-3 million globally due to greater compliance risks and data sensitivity.
A key takeaway: The longer it takes to contain a breach, the higher the long-term expense. Breaches with a lifecycle longer than 200 days, for example, exceeded $5 million in total costs worldwide.
Proactive investments in AI-powered cybersecurity tools, incident response planning, and breach containment can drastically reduce your long-term financial fallout.
Step 3: Calculate your cybersecurity ROI
To give you a clear picture of how to measure cybersecurity ROI, let’s walk through a sample analysis with high-level data.
Here’s the formula we recommend for calculating cybersecurity ROI:

Now, consider that the average security budget for a middle-market organization is $3.4 million (IANS 2025 CISO Compensation and Budget Report), while the average cost of a data breach in the U.S. is $10.22 million (IBM).
Given that over 80% of organizations experienced at least one successful attack in the past year (CyberEdge Group 2024 Cyberthreat Defense Report), cybersecurity ROI can be calculated as follows:
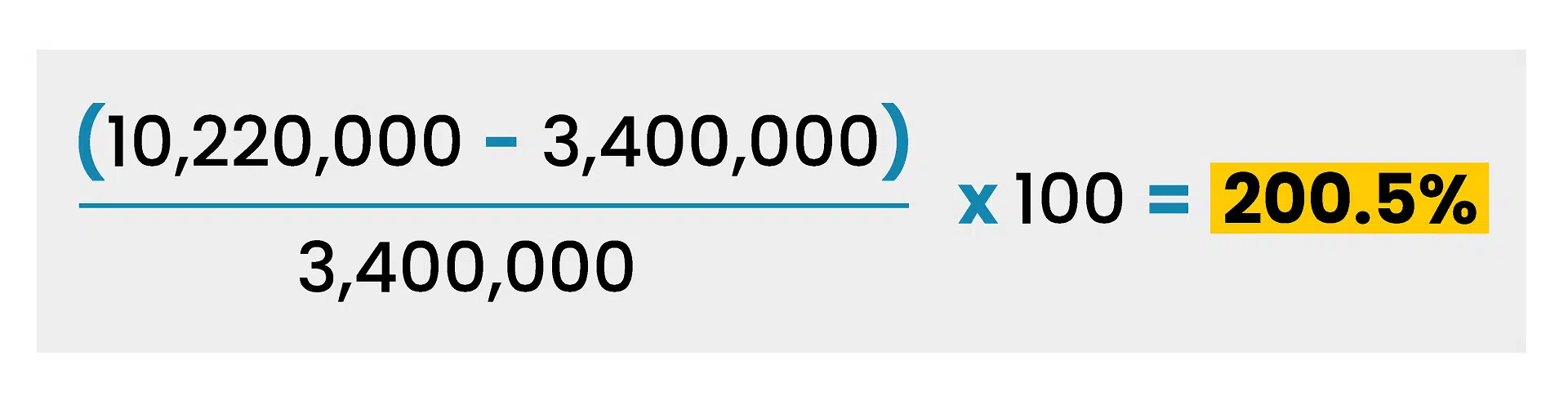
In other words, preventing just one data breach yields a 200.5% return on its cybersecurity investments for this middle-market organization, given the company invests in the right AI tools, talent, and building the correct processes.
Of course, this is a simplified illustration. Your actual ROI will depend on your budget, risk profile, threat landscape, and unique business circumstances. But the message is clear: cybersecurity ROI is too large to ignore.
10 key metrics for measuring cybersecurity effectiveness
Establishing cybersecurity benchmarks and key performance indicators (KPIs) is another critical part of building a resilient security posture. These metrics play a pivotal role in justifying spending, prioritizing investments that meaningfully reduce risk and protect business value, and showcasing the effectiveness of security measures to stakeholders.
Organizations cite investment in cybersecurity as a key differentiator for competitive advantage, with 57% citing customer trust and 49% citing brand integrity and loyalty as areas of influence, according to PwC’s 2025 Global Trust Insights survey.
Below are some of the most common benchmarks employed by organizations to assess the health of their cybersecurity strategy:
- Mean time to detect (MTTD)
The average time it takes to identify or become aware of a cybersecurity threat or breach after it has occurred. MTTD evaluates how quickly your detection systems and processes can recognize breaches. The lower the number, the stronger your security stance. - Mean time to resolve (MTTR)
The average time it takes to fully resolve a cybersecurity incident from the moment it is detected to when it is completely contained and remediated, and normal operations are restored. MTTR reflects the effectiveness and speed of an organization’s incident response. A lower MTTR indicates a more efficient response and less exposure. - Reduction in downtime
The reduction in downtime for critical systems, applications, or services after cybersecurity solutions are implemented. A strong cybersecurity strategy should result in faster threat detection and response, minimizing disruption and downtime. - False positive rate
The percentage of alerts flagged as threats that turn out to be harmless. Keeping the “noise” in your security alerts low is essential to focus resources on genuine incidents. - Cost per incident
The total financial impact of each security incident, including downtime costs, investigation costs, employee productivity loss, etc. - Percentage of intrusions prevented
The proportion of attempted cyber intrusions or attacks that are detected and blocked successfully before causing harm. - Vulnerability patching rate
The average number of calendar days it takes to apply security patches after they are released. Exploited non-patched vulnerabilities now account for a fifth of all breaches, Verizon’s 2025 Data Breach Investigations Report found, highlighting the urgent need for faster patching. - Reduction in insurance premiums
Insurance providers assess various factors before determining premiums, such as the presence of robust security controls, AI-driven threat detection tools, employee training programs, incident response plans, and regulatory compliance. A reduction in your cyber insurance premium is a strong indicator that your security strategy is considered effective and lower risk by insurers. - Security awareness and training completion rate
The percentage of employees completing required cybersecurity training within a specific timeframe, reflecting how well your workforce is prepared to spot and stop threats like phishing, social engineering, and password misuse. With human error driving 95% of breaches in 2024 (Mimecast State of Human Risk 2025), regular training is essential.
Why Auxis: Maximizing security ROI with a top-tier MSSP
As cyberattacks grow more frequent, sophisticated, and costly in the era of AI, a strong, proactive security posture is no longer optional – it’s a business necessity.
But building and maintaining a cybersecurity program with the right tools, talent, and processes is still expensive and complex – especially for small and mid-sized organizations.
Partnering with a trusted managed security services provider like Auxis gives you instant access to top-tier cybersecurity talent, enterprise-grade protection, and best practices without the cost and headache of building extensive security operations in-house.
With nearly 30 years of experience, Auxis delivers end-to-end managed security solutions powered by AI, automation, and top-tier nearshore talent at our Security Operations Center in Latin America – powering 24/7 proactive protection, significant cost savings, and rapid threat response. We’ll also help you analyze your specific business risk – and translate those insights into a compelling business case for the security investments you want to prioritize.
The result? Stronger security, maximum IT security ROI, and clear insight into the value delivered across your organization.
Want to strengthen your cybersecurity stance with expert-driven protection? Schedule a consultation with our cybersecurity experts today! You can also visit our resource center for more cybersecurity tips, strategies, and success stories.
Frequently Asked Questions
What is cybersecurity ROI and why should I measure it?
How can IT security ROI be maximized in a complex technology environment?
How can I measure the ROI of preventing downtime or data loss?
How can I maximize IT security ROI while managing budget constraints?
What is managed cybersecurity ROI and how does it compare to in-house security?



